Last week we alerted our insurance colleagues to multiple instances of spear-phishing as they relate to a new trend toward using OneDrive as a means of spreading phishing attacks. Today I’d like to take a few minutes to provide you with some easy ways to help protect you and your company against phishing attacks.
The goal of these types of phishing attacks are two-fold: one, they want your email username and password, or two, they want to give you malware. In the past six months, Cyber Defense Institute has seen both, with devestating consequences.
For those in the Insurance industry, we’ve been told by the DFS superintendant that: “ the majority of successful breaches… have involved phishing attacks, social engineering threats, and issues relating to password composition and security and email security.” The superintendant goes on to say:
More specifically, a significant number of the events reported to DFS involved breaches that stemmed from employees providing credentials in response to attractive emails that trick a user to provide confidential information. In these cases, the intruder sends a legitimate-seeming e-mail to a company's employee or employees. These attacks are carefully planned to appear from a source that the employee will trust, perhaps even appear to be an email from a customer or client of that employee and a subject that will peak their interest. The employee is prompted 2 to enter his or her e-mail credentials, and the intruder gains access to the company's e-mails on the system, which can contain consumers' personal identifying information.
If you’re interested in seing what the whole attack looked like, look at this article I previously posted
So, we know the threat is real, but what can we do about it. Here is a list of specific, actionable things you can do to protect yourself:
Security Awareness Training
One of the best things we can do is train our employees on what to look for in a phishing email. In our opinion, this training should be ongoing and multi-faceted. We sell KnowBe4 security awareness training because we can provide our users with frequent phishing tests, weekly security newletters, training content, and much more,
What to do
Ensure you provide frequent Security Awareness Training. We recomend bi-weekly phishing tests, quarterly or even monthly training videos, and weekly newsletters. We also recomend conversations in meetings, and having an teamwork approach to questionable email.
If you don’t have a robust program, contact us and we can get you a quote for KnowBe4, or click here for more information on KnowBe4, including a free trial.
Two-Factor Authentication
After security awareness training, two-factor authentication is incredibly reliable at protecting your email. If you have Office 365, two-factor authentication is FREE and it is not as burdensome as you may think. You are not required to enter a code from your phone every time you open your email. That’s a misnomer.
In reality, you enter the code ONCE for Outlook, and you enter the code ONCE if you use the Outlook app for your phone. If you log into Outlook Web Access or any of the other Microsoft 365 products, you can configure Microsoft to remember your login for any number of days.
What to do
For Office 365, here is the docuemntation: https://support.office.com/en-gb/article/set-up-2-step-verification-for-office-365-ace1d096-61e5-449b-a875-58eb3d74de14
For G-Suite: https://support.google.com/a/answer/9176657?hl=en
For hosted Exchange you will need to add an OAUTH provider such as Duo, and taht’s way outside the scope of this post
Don’t Store Sensitive Data
You can’t fully control what comes into your inbox, but you can control what you do with that data. Having sensitive data in your email can pose a serious threat. If your email is compromised and it contains sensitive information, the data usually has to be considered breached, and therefor reportable. If you don’t have sensitive emails, you don’t have a breach (however, in DFS world you still have to report a compromised email account).
What to do
Don’t SEND sensitive information through email such as credit card numbers, health information, SSNs, etc.
If you RECEIVE sensitive email:
Delete the email
Contact the sender and ask them to not send sensitive data. Ask them to encrypt it, fax it, or use a “proper channel”
Implement Data Loss Prevention (DLP) technologies. I admit this isn’t always easy for small companies, but some Anti-Virus and Email Protection products include this feature. Ideally, your spam filter should be able to look for, and block sensitive data such as credit card numbers, SSN’s health information or even account numbers.
Advanced Threat Protection
Default spam filters that come with Office 365 and Gmail provide some coverage, but not enough. Exchange offers no protection. With Advanced Threat Protection or ATP, your spam filter will do additional checks on your incoming email such as “clicking” on the links and opening any attachments to see if they’re safe. I admit, ATP isn’t able to get around the OneDrive attack that opened this post, but it’s still important.
What to do
For Office 365 add “Advanced Threat Protection” to your account. It’s $1 per user, per year (https://docs.microsoft.com/en-us/office365/securitycompliance/office-365-atp )
For G-Suite, enable the :enhanced” protections (https://support.google.com/a/answer/7577854?hl=en )
Alternatively, purchase a spam system such as Barracuda, Sophos, or ProofPoint
Anti-Malware
Make sure you have agood anti-virus protection. And by good, I mean one that you purchased. Ideally, it should be centrally managed (cloud is better), and have Advanced Threat Protection and web protection. In the case of the attacks from last week, my anti-virus and firewall’s web protection blocked one of the two attacks. 50% is pretty poor, but it’s a start.
What to do
Purchase Anti-Malware that includes web protection
Purchase so called “Next Generation Anti-Malware.” Other terms include “Deep learning”, “Endpoint Detection and Response”, etc.
Add Advanced Threat Protection to your firewall that looks for bad URLs
Example of Next Generation products include Sophos Central with Intercept X, Carbon Black., Cylance, or TrendMicro XGen
Anti-Spoofing
Some of these attacks take advantage of misconfigured (or non-configured) DNS records that are meant to prevent spoofing. By properly configuring Anti-Spoofing on your email domain spammers can’t send emails that look like they came from your domain. This has two benefits: you can’t receive emails that spoof your domain, and the rest of teh world can’t either.
What to do
Configure SPF, DKIM, and DMARC dns records for your email. Explainign these are far outside the scope of this post, but pass it along to your system administrator. If you’re really interested, here is a post that explains it all: https://www.bettercloud.com/monitor/spf-dkim-dmarc-email-security/
Office 365 Secure Score and Login Branding
If you have Office 365, Microsoft offers “Secure Score” which is set of scored configuration options that better protection your email and Office 365 environment. By making suggested changes, you increase your score and therefore increase your security.
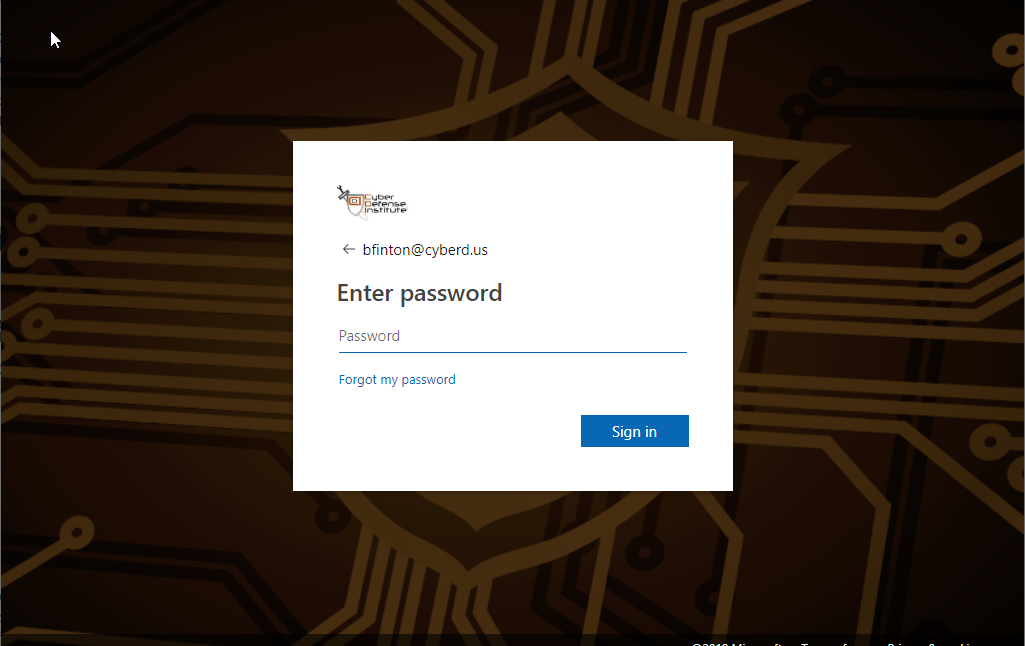
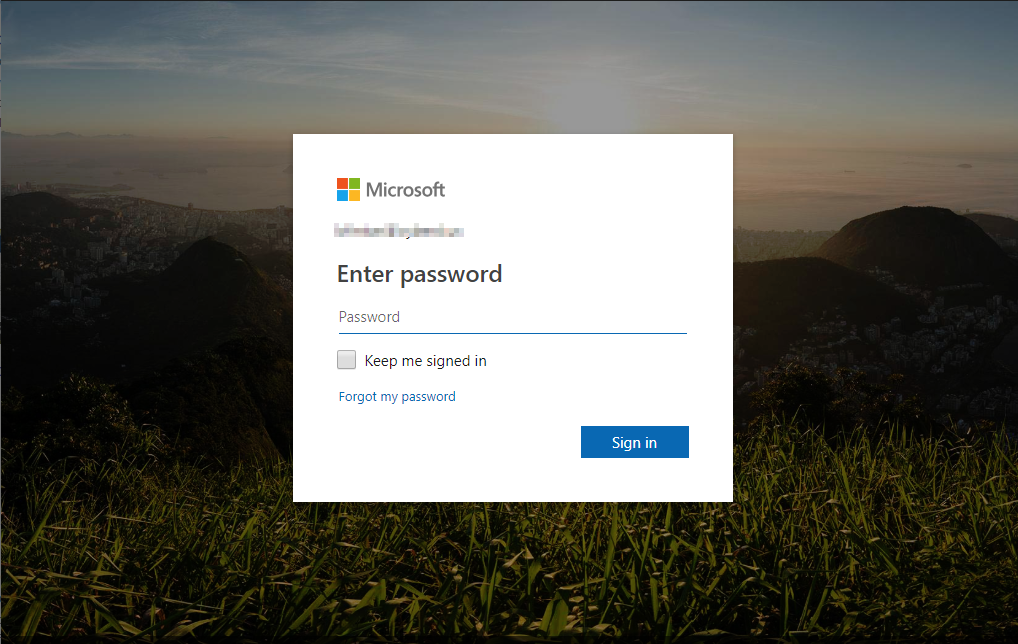
Also, Microsoft allows you to “brand” your Office 365 login page with your company logo and custom background. This is extremely helpful because phishing emails target you by making the login screen look like Microsoft’s login page to get you to enter your password. However, if you’ve branded your login screen, users will know to look for your background picture and logo. Here’s an example of how Cyber Defense Institute brands our logon page, as well as what it looks like unbranded
Branded
Unbranded
What to Do
For Microsoft Secure Score, go to https://learn.microsoft.com/en-us/microsoft-365/security/defender/microsoft-secure-score?view=o365-worldwide
For branding instructions, go to https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/customize-branding
Audit
If an account is compromised, audditing of the account is going to be extremely important to determine if a breach occured, and what data was accessed. Without auditting, it must be assumed that all sensitive data in a compromised email account has been breached, and therefore reported. With auditting, it’s possible to contain a compromised account to just that, and not a breach (although it;s reportable if you’re DFS regulated).
What to do
For Office 365, https://docs.microsoft.com/en-us/office365/securitycompliance/enable-mailbox-auditing
For G-Suite it’s already on